If you have concerns regarding potential eavesdropping/bugging, Valkyrie would suggest that TSCM sweeping of all potentially vulnerable locations takes place (offices, residences, vehicles, aircraft etc.). Valkyrie can perform sweeping as an independent activity without performing a wider ranging security assessment of the offices, residencies, lifestyle etc. However (threat dependant – physical/technical) in most cases we suggest a general (physical) security assessment is also conducted.
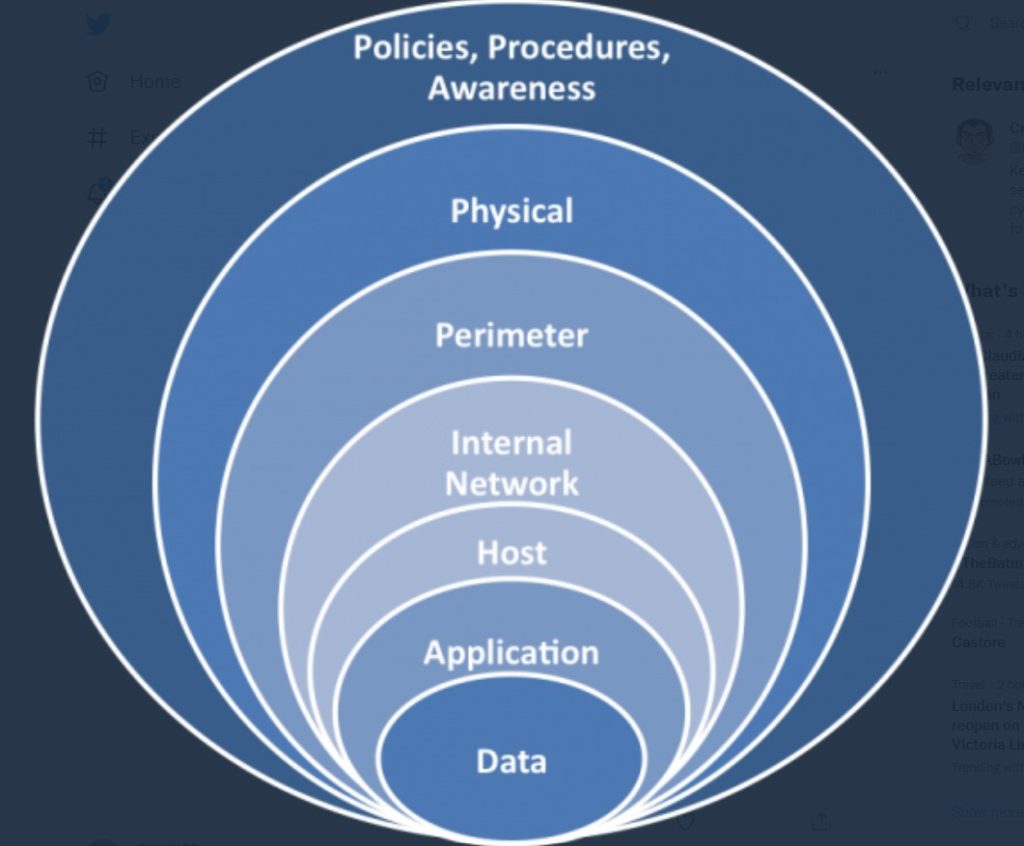
Security is best assessed and structured by a ‘layered approach method’ (see diagram) with the inner layers being the internal systems (network/data etc.) and sweeping and Cyber security activity may well provide a clean bill of health for the inner layer(s). However, in our experience, it would be unwise to only assess the inner layers and not the outer layers (‘the physical’, areas such as – doors/windows, locks, CCTV, perimeters, access control, alarms etc.) as it will likely leave the inner layers vulnerable to future attack.
Implementing a layered approach to security increases the work factor for an attacker, in other words – it adds more time and effort to conduct an attack – good outer security will increase the likelihood of an attack being compromised and failing before they reach the inner layers. Strong outer layers also act as a considerable deterrent to would-be-attackers (‘Deter-Detect-Deny-Delay-Defend’).
The outer layer (policies, procedures, awareness) is also very important and should not be overlooked, these are vital to all layers and underpin the overall security strategy. In addition ‘security awareness training’ can be another significant component to security strategy, generally most people have not received any form of security training and don’t pick up on potential suspicious incidents or activity – highlighting the activity/tactics of criminals and how they operate to employees can be highly effective.
Another consideration often overlooked is the ‘human factor’, unfortunately humans are more often than not the most vulnerable part of a security strategy, this can be for a host of reasons but an example of a possible scenario might be – employees operating on behalf of an adversary are offered a financial incentive to report back/conduct tasks on their behalf, such as placing eavesdropping devices in an office or residence, this would be especially concerning if the employee had trusted access to key individuals/private areas. This potential scenario (other similar ones) should not be discounted especially if up against a determined adversary. To counter this potential scenario (in addition to vetting) robust procedures should be in place e.g. for access to meetings and phone conversations (need to know basis).
Final point, key-individuals should be conscious of their lifestyle and how they go about their daily business, are they ‘security aware’ in all they do or does their daily routine leave them vulnerable.